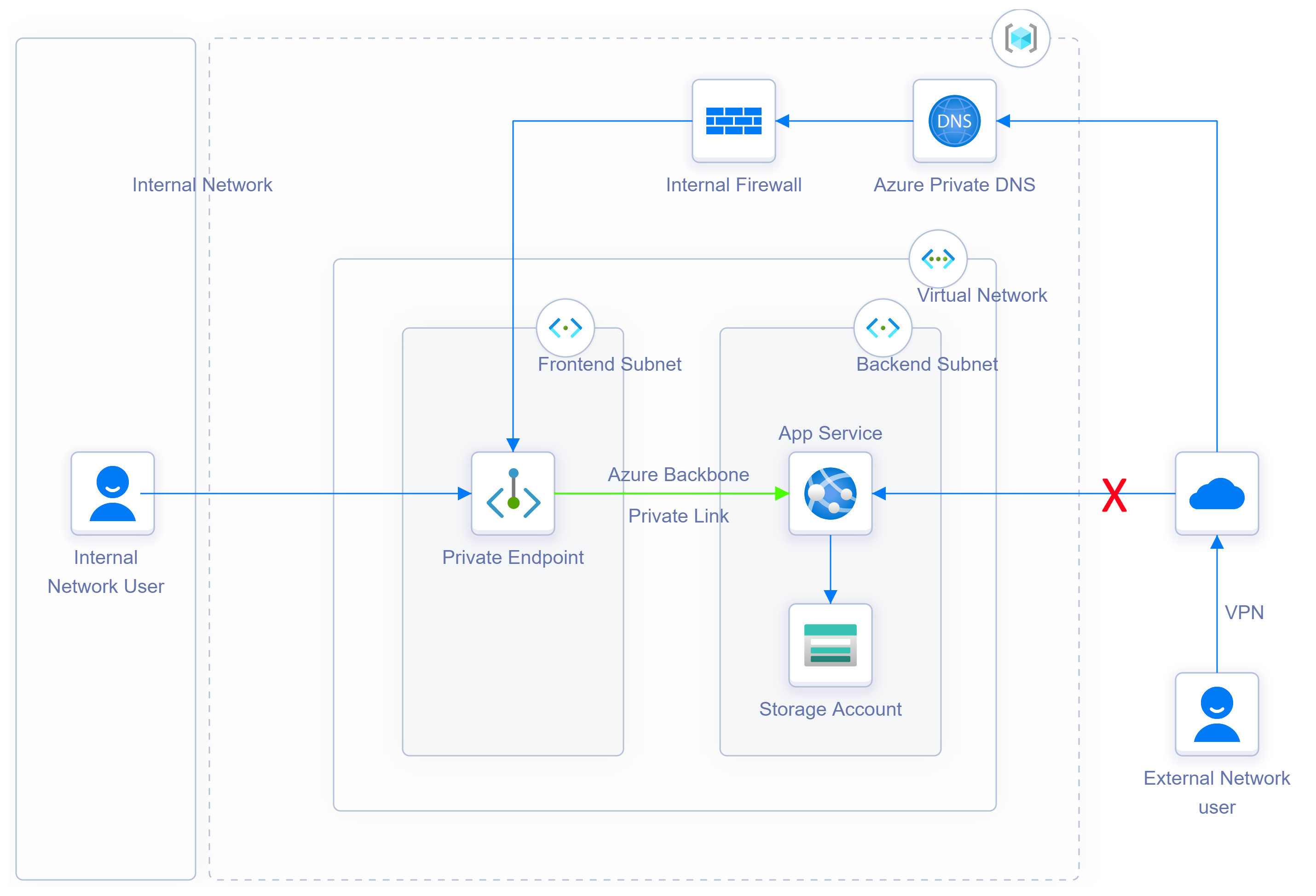
Azure Private Endpoint on App Service and Secure Access to Storage Account
Usually when we provision App service on Azure, the web app is available to the whole world. However, there might be times when you need to secure the web app and make it accessible only from your internal/corporate network.
There are multiple ways you can achieve this objective, for example, you can introduce an Azure Application gateway with a private IP frontend and with backend pool targeting your App service. Another approach is to host the App Service behind the Azure WAF, one more approach is to host the App Service behind Azure Front Door. All these techniques have pros and cons, and the cost can vary depending on the tier you are selecting and data transfer.
One new approach is to use the Azure Private endpoint along with Virtual Network
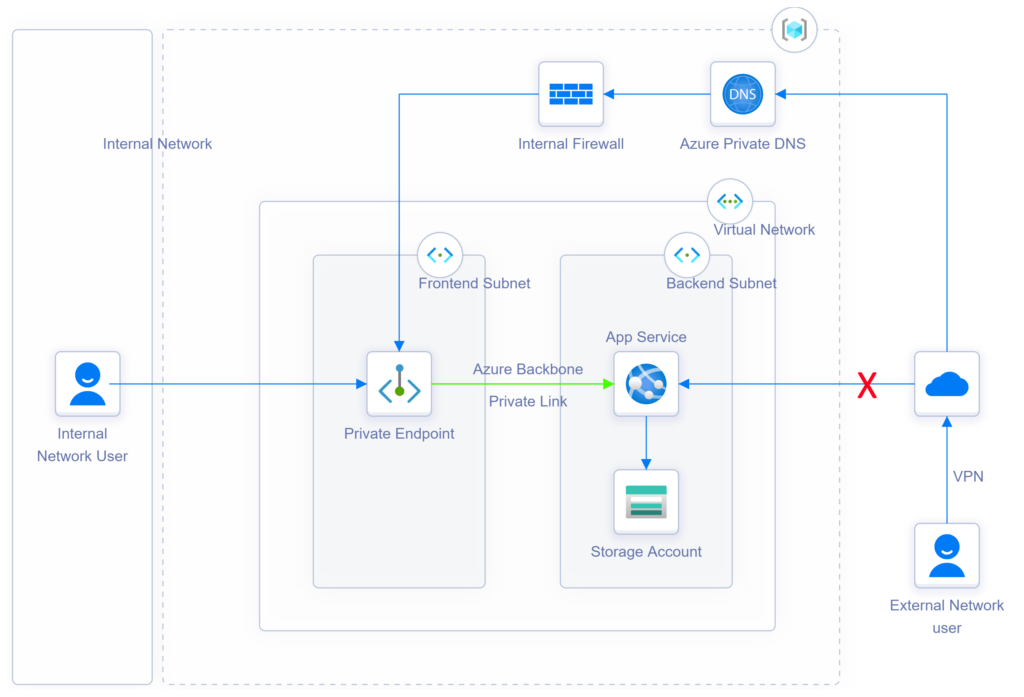
DNS Resolution Flow:
1. DNS Query for azcrudoperationapp.azurewebsites.net
2. Authoritative DNS query for azcrudoperationapp.azurewebsites.net
Response: CNAME azcrudoperationapp.privatelink.azurewebsites.net
3. DNS Query for azcrudoperationapp.privatelink.azurewebsites.net
Response: Private IP address 10.1.3.4
4. Response: CNAME azcrudoperationapp.privatelink.azurewebsites.net
A azcrudoperationapp.privatelink.azurewebsites.net 10.1.3.4
5. Dedicated connection to app service through the private end point (10.1.3.4) over the Microsoft Backbone
Steps which I followed:
- Create a New App Service or Change an existing App Service to a Premium tier if not.
- Create a new Virtual Network or use an existing Virtual Network
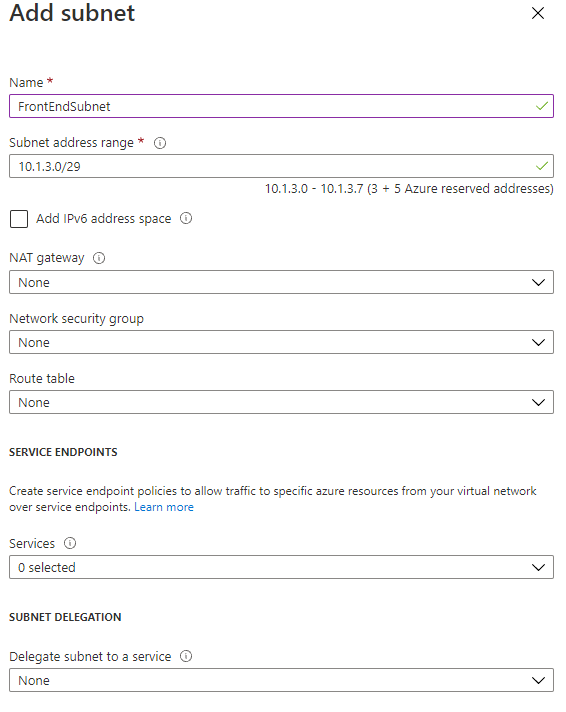
- Create two Subnets in the Virtual Network
- One Subnet (/29) for the Private endpoint
- One Subnet (/29) for the App Service and Storage Account

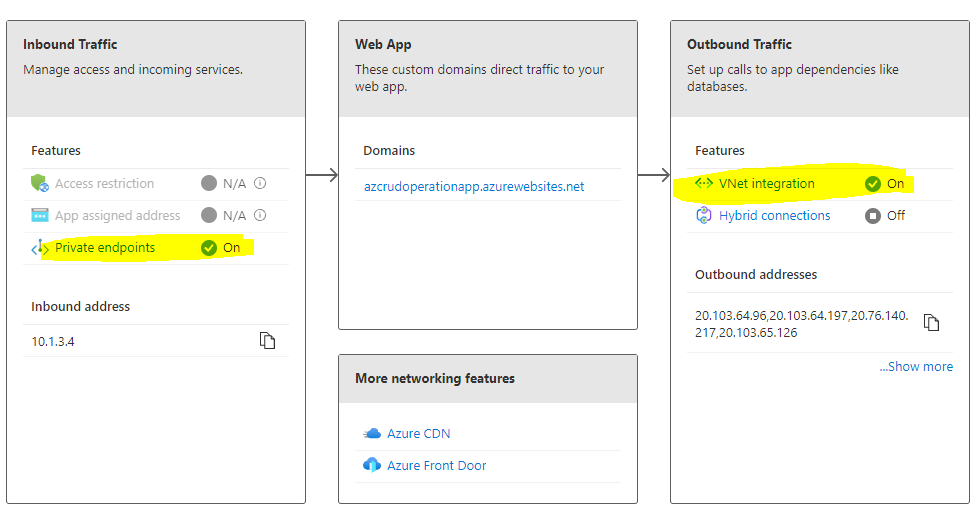
- Configure App Service with Private endpoint. Use the Frontend subnet created earlier.

- Configure App Service with Virtual Network Integration. Use the Backend subnet created earlier.

- Now the App Service Networking section should look like the below
- Now we need to configure the Networking section of the Storage account.
- Modify “Allow Access from All Networks” to “Selected Networks”
- Add the Virtual Network and the same Backend subnet created earlier.

- The Networking section of Storage account should look like the below:

- Also, we must disable the “Route All” in the Virtual Network Integration of the App Service.

- Now if you access the website from public/external network, we will see that the website is not accessible

- If you access the website from the corporate/internal network, we should see the website

In Summary, through Private Endpoint, we can now secure the App Service and Storage account through a virtual network.